In today's interconnected world, the proliferation of Internet of Things (IoT) devices has opened up unprecedented opportunities, yet it has simultaneously introduced complex security challenges. Managing and accessing these devices remotely, especially in sensitive or mission-critical environments, demands a robust and secure infrastructure. This is where the synergy of remoteiot vpc ssh aws becomes not just beneficial, but absolutely essential for maintaining operational integrity and data confidentiality. From industrial sensors to smart city infrastructure, ensuring that remote IoT devices are both accessible for management and impenetrable to malicious actors is paramount. Without a well-architected security framework, the very advantages of IoT can quickly turn into significant vulnerabilities, leading to data breaches, operational disruptions, or even physical harm.
The journey to secure remote IoT deployments involves navigating a landscape of network isolation, secure authentication, and robust access controls. AWS, with its comprehensive suite of cloud services, offers the foundational building blocks to achieve this. By leveraging Amazon Virtual Private Cloud (VPC) for network segmentation and SSH (Secure Shell) for encrypted communication, organizations can establish a fortress around their remote IoT ecosystems. This article will delve deep into how these powerful AWS capabilities, combined with meticulous planning and adherence to security best practices, empower businesses to manage their remote IoT devices with confidence and peace of mind.
The Evolving Landscape of IoT Security
The Internet of Things (IoT) is no longer a futuristic concept; it's an omnipresent reality, transforming industries from manufacturing and healthcare to smart homes and agriculture. However, this pervasive connectivity brings with it an increasingly complex security landscape. Unlike traditional IT systems, IoT devices often operate with limited processing power, memory, and battery life, making it challenging to implement sophisticated security measures directly on the device. Furthermore, they are frequently deployed in remote, unsupervised locations, making them prime targets for cyberattacks. The sheer volume and diversity of IoT devices also create a vast attack surface, demanding a comprehensive and scalable security strategy. Threats to IoT devices range from denial-of-service (DoS) attacks and data exfiltration to unauthorized remote control and device hijacking. A compromised IoT device can serve as an entry point into an entire network, leading to broader system compromises. Consider an industrial IoT sensor: if breached, it could provide an attacker with access to critical operational technology (OT) networks, potentially causing physical damage or production halts. This necessitates a proactive and layered security approach, focusing not just on the devices themselves, but on the entire communication pathway and the underlying infrastructure. Understanding these evolving threats is the first step in building a resilient **remoteiot vpc ssh aws** architecture that can withstand sophisticated attacks and ensure the continuous, secure operation of your connected devices.Understanding AWS VPC for IoT Isolation
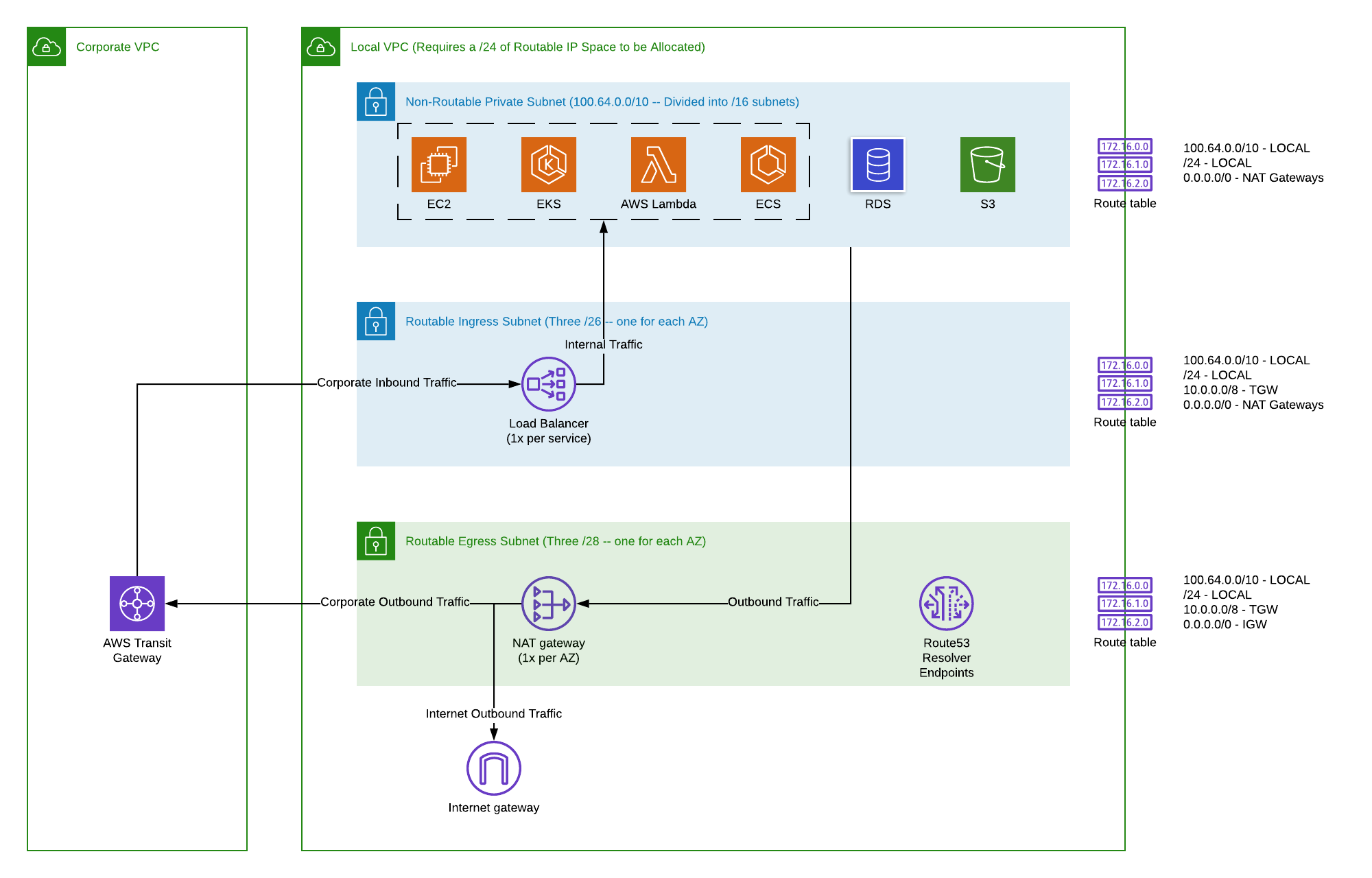
Amazon Virtual Private Cloud (VPC) serves as the cornerstone of network security and isolation within the AWS ecosystem. Essentially, a VPC is a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. This isolation is crucial for IoT deployments, as it allows you to create a private, secure environment for your devices, separate from the public internet and other AWS customers' resources. Within your VPC, you have complete control over your virtual networking environment, including IP address ranges, subnets, route tables, and network gateways. This level of control is fundamental for implementing a robust **remoteiot vpc ssh aws** strategy. For remote IoT devices, a VPC provides a dedicated, private network space where device communication can be strictly controlled. Instead of devices communicating directly over the public internet, they can establish secure connections to resources within your VPC. This significantly reduces the attack surface, as unauthorized access attempts are blocked at the VPC boundary. By carefully designing your VPC, you can segment your IoT network, ensuring that different types of devices or different operational functions are isolated from each other, preventing lateral movement in case of a breach. This granular control over network traffic is indispensable for any serious IoT deployment aiming for high security and reliability.Subnetting and Network ACLs for Granular Control
Within an AWS VPC, subnetting and Network Access Control Lists (ACLs) are powerful tools for achieving granular control over network traffic, especially vital for **remoteiot vpc ssh aws** security. Subnets allow you to divide your VPC into smaller, isolated network segments. You can create public subnets for resources that need direct internet access (like a NAT Gateway for outbound connections from private subnets) and private subnets for resources that should not be directly accessible from the internet (such as your IoT device management servers or data processing instances). This segmentation ensures that your most critical IoT infrastructure components reside in protected areas. Network ACLs act as stateless firewalls at the subnet level, providing an additional layer of security beyond security groups (which are stateful and operate at the instance level). While security groups permit or deny traffic to specific instances, Network ACLs permit or deny traffic to and from entire subnets. You can define highly specific rules based on IP addresses, ports, and protocols for both inbound and outbound traffic. For instance, you could configure a Network ACL to only allow SSH (port 22) traffic from a specific IP range representing your administrative network, effectively blocking all other SSH attempts from unknown sources. This dual-layer approach, combining subnets for logical separation and Network ACLs for strict traffic filtering, significantly enhances the security posture of your IoT network within AWS.Secure Connectivity with SSH for Remote IoT Devices
Secure Shell (SSH) is a cryptographic network protocol that enables secure remote login and command-line execution between two networked devices. For remote IoT devices, SSH is the de facto standard for secure access, offering strong encryption to protect data in transit and robust authentication mechanisms. When integrating SSH into your **remoteiot vpc ssh aws** architecture, you are essentially creating a secure tunnel for managing, troubleshooting, and updating your devices from a central location. This is particularly critical for devices deployed in remote or untrusted environments where physical access is impractical or impossible. The primary benefit of SSH lies in its ability to encrypt all communication between the client (your management workstation) and the server (your IoT device or an intermediary bastion host). This encryption prevents eavesdropping, tampering, and connection hijacking. Furthermore, SSH supports various authentication methods, with public-key cryptography being the most secure and recommended approach. Instead of relying on passwords, which can be brute-forced or guessed, public-key authentication uses a pair of cryptographic keys: a public key stored on the device and a private key kept securely by the user. This method provides a much higher level of security, making it extremely difficult for unauthorized users to gain access. Implementing SSH correctly is a cornerstone of maintaining control and security over your distributed IoT fleet.Managing SSH Keys and Best Practices
Effective management of SSH keys is paramount for the security of your **remoteiot vpc ssh aws** deployments. Unlike passwords, SSH private keys are extremely sensitive; if compromised, an attacker can gain unauthorized access to any system where the corresponding public key is authorized. Therefore, treating your private keys with the utmost care is non-negotiable. As the "Data Kalimat" reminds us, "Keep your password a secret at all times." This principle applies even more strongly to private SSH keys. Best practices for SSH key management include: * **Generate Strong Keys:** Always use strong cryptographic algorithms (e.g., RSA 2048-bit or higher, or ED25519) when generating keys. * **Protect Private Keys:** Store private keys in a secure location, ideally on a hardware security module (HSM) or a password-protected key manager. Encrypt private keys with a strong passphrase. * **Regular Rotation:** Periodically rotate SSH keys, especially for long-lived deployments or if there's any suspicion of compromise. * **Least Privilege:** Grant SSH access only to necessary users and for specific purposes. Limit the public key's permissions on the server side (e.g., restrict commands). * **Bastion Hosts:** For highly sensitive environments, use a bastion host (also known as a jump box) within your VPC. This is a hardened server that acts as an intermediary, allowing SSH connections only from trusted IP addresses and then forwarding those connections to your private IoT devices. This significantly reduces the direct exposure of your devices. * **Monitoring and Logging:** Implement robust logging and monitoring for all SSH access attempts. AWS CloudTrail and VPC Flow Logs can help track network activity and SSH connections, alerting you to unusual patterns. By adhering to these practices, you can significantly mitigate the risks associated with remote access and ensure that only authorized personnel can securely interact with your IoT devices.Integrating Remote IoT Devices with AWS Services
Beyond basic connectivity and secure shell access, the true power of **remoteiot vpc ssh aws** lies in its integration with the broader AWS ecosystem. AWS IoT Core acts as the central hub for connecting and managing billions of IoT devices, allowing them to securely interact with other AWS services. Devices can publish telemetry data to IoT Core, which then routes it to services like AWS Lambda for serverless processing, Amazon S3 for data storage, Amazon DynamoDB for NoSQL databases, or Amazon Kinesis for real-time data streaming. This seamless integration enables powerful analytics, machine learning, and automation capabilities based on your IoT data. Furthermore, AWS IoT Device Management provides tools for managing your fleet, including remote updates, monitoring device health, and troubleshooting. For devices that require more direct interaction or specialized software, AWS Systems Manager can be used in conjunction with SSH to manage operating systems, apply patches, and install applications. This holistic approach ensures that your remote IoT devices are not just connected and secure, but also fully integrated into a scalable, cloud-native architecture that can adapt to evolving business needs. The ability to leverage the full spectrum of AWS services, from data ingestion to advanced analytics and device lifecycle management, transforms raw device data into actionable insights and operational efficiencies.Building a Secure Remote IoT Architecture with AWS
Constructing a secure **remoteiot vpc ssh aws** architecture requires a methodical approach, integrating various AWS services to create a layered defense. The core principle is to minimize the attack surface and enforce the principle of least privilege. Your architecture should begin with a well-designed VPC, segmented into public and private subnets. IoT devices, especially those that do not need direct inbound internet access, should reside in private subnets. Outbound internet access for these devices can be routed through a NAT Gateway in a public subnet. For remote management, a bastion host or a secure VPN connection into the VPC is crucial. SSH connections should terminate at this bastion host, which then forwards the connection to the target IoT device or an intermediary management server within a private subnet. This setup prevents direct SSH access to your IoT devices from the public internet. AWS IoT Core should be used for device authentication and secure communication channels, leveraging X.509 certificates or AWS IoT Device Defender for continuous security monitoring. IAM roles and policies must be meticulously defined to control access to AWS resources, ensuring that devices and users only have the permissions they absolutely need. This comprehensive architectural approach builds a robust foundation for secure and scalable remote IoT operations.Bridging On-Premise Devices to AWS VPC
Many IoT deployments involve devices that are already on-premise or in private networks, and bridging these devices securely to an AWS VPC is a common requirement for **remoteiot vpc ssh aws** strategies. AWS provides several robust options for establishing secure connectivity between your on-premise network and your VPC, effectively extending your private cloud environment to your physical locations. The primary methods include: * **AWS Site-to-Site VPN:** This creates an encrypted tunnel between your on-premise network (via a customer gateway) and your AWS VPC (via a virtual private gateway). It's a cost-effective and secure way to connect multiple on-premise locations to your VPC over the public internet. All traffic is encrypted, providing confidentiality and integrity. * **AWS Direct Connect:** For dedicated, high-bandwidth, and low-latency connections, Direct Connect establishes a private network connection from your premises directly to AWS. This bypasses the public internet entirely, offering enhanced security and predictable performance, ideal for large-scale IoT data ingestion or critical remote device management. * **AWS IoT Greengrass:** For edge devices, Greengrass extends AWS capabilities to local devices, allowing them to perform local compute, messaging, data caching, sync, and machine learning inference. It can connect to AWS IoT Core and other AWS services, effectively bridging the gap between local processing and cloud intelligence, even with intermittent connectivity. By utilizing these services, organizations can seamlessly integrate their existing on-premise IoT infrastructure with the secure and scalable environment of an AWS VPC, enabling centralized management, data processing, and analytics for their entire IoT fleet, regardless of physical location.Troubleshooting Common Remote IoT VPC SSH AWS Issues
Even with a meticulously planned architecture, issues can arise when managing **remoteiot vpc ssh aws** environments. Effective troubleshooting is key to minimizing downtime and maintaining operational continuity. Common problems often revolve around connectivity, authentication, and permissions. If you encounter issues connecting via SSH to a remote IoT device or an instance within your VPC, consider the following: * **Network Connectivity:** Verify that your VPC's route tables are correctly configured, allowing traffic to flow between your management host and the target device's subnet. Check Network ACLs and security groups to ensure they permit SSH traffic (port 22) from your source IP address. * **Device Status:** Confirm the IoT device is powered on, connected to the network, and its SSH server is running. * **Firewall Rules:** Ensure no local firewall rules on the IoT device itself are blocking incoming SSH connections. * **Public IP/Elastic IP:** If connecting directly from the internet (not recommended for private subnets), ensure the instance has a public IP or Elastic IP associated with it. * **Subnet Type:** Remember, devices in private subnets cannot be directly accessed from the internet. You'll need a bastion host or VPN. * **Security Group Rules:** Double-check that the security group attached to your instance/device allows inbound SSH traffic from your source IP.Ensuring Proper IAM Roles and Security Group Configurations
Incorrect IAM roles and security group configurations are frequent culprits behind connectivity issues in **remoteiot vpc ssh aws** setups. IAM (Identity and Access Management) defines who can do what within your AWS account, while security groups act as virtual firewalls for your instances. * **IAM Roles and Policies:** * **"You may not have activated your utorid and password"** – In an AWS context, this translates to ensuring your IAM user or role has the necessary permissions. Verify that the IAM user attempting the SSH connection has the correct permissions to access the EC2 instance (if using an EC2 instance as a bastion host or for management) or the specific IoT device. * If using AWS Systems Manager Session Manager (a good alternative to direct SSH for EC2 instances), ensure the EC2 instance has an IAM role with the `AmazonSSMManagedInstanceCore` policy attached. * For IoT devices interacting with AWS IoT Core, ensure their certificates and policies are correctly attached and grant appropriate publish/subscribe permissions. * **Security Group Configurations:** * **Inbound Rules:** For SSH access, the security group attached to your target instance (e.g., bastion host, management server, or even the IoT device if directly accessible) *must* have an inbound rule allowing TCP traffic on port 22. The source of this rule should be restricted to your specific IP address, your corporate network's IP range, or the security group of your bastion host (if chaining connections). Avoid `0.0.0.0/0` for SSH unless absolutely necessary and coupled with other strong controls. * **Outbound Rules:** While less common for SSH *inbound* issues, ensure outbound rules are not overly restrictive, preventing necessary responses. Typically, security groups allow all outbound traffic by default, but custom configurations might block it. * **Associated Security Groups:** Verify that the correct security group is actually associated with the network interface of your target instance or device. By systematically reviewing these configurations, you can quickly pinpoint and resolve most common access and connectivity problems, ensuring your remote IoT operations remain secure and uninterrupted.Advanced Security Considerations for Remote IoT Deployments
Beyond the foundational aspects of **remoteiot vpc ssh aws**, advanced security considerations are crucial for truly resilient IoT deployments. As the threat landscape evolves, so too must your defenses. Implementing a comprehensive security strategy involves continuous monitoring, proactive threat detection, and robust incident response capabilities. * **Zero Trust Architecture:** Adopt a Zero Trust model, where no entity (user, device, application) is inherently trusted, regardless of its location. Every access request must be authenticated and authorized. * **Vulnerability Management:** Regularly scan IoT devices and associated infrastructure for vulnerabilities. Implement a patch management strategy to ensure devices are updated with the latest security fixes. * **Intrusion Detection and Prevention Systems (IDPS):** Deploy IDPS within your VPC to detect and prevent malicious activities. AWS Network Firewall and third-party solutions can provide this capability. * **Data Encryption at Rest and in Transit:** Ensure all sensitive IoT data is encrypted both when stored (at rest) using services like S3 or RDS with encryption enabled, and when transmitted (in transit) using TLS/SSL for communication channels and SSH for management. * **Logging and Auditing:** Enable comprehensive logging across all AWS services involved in your IoT solution (CloudTrail, VPC Flow Logs, IoT Core logs). Centralize logs in Amazon CloudWatch Logs or S3 for analysis and auditing. * **AWS IoT Device Defender:** Leverage AWS IoT Device Defender for continuous security monitoring of your IoT devices. It can detect anomalies in device behavior, identify security misconfigurations, and alert you to potential compromises. * **Security Automation:** Automate security tasks, such as incident response, vulnerability scanning, and policy enforcement, using AWS Lambda and other automation tools. By integrating these advanced considerations, organizations can elevate their remote IoT security posture, safeguarding against sophisticated attacks and ensuring the long-term integrity and reliability of their connected ecosystems.The Future of Secure Remote IoT
The trajectory of IoT is one of continuous growth and increasing complexity, making the secure management of **remoteiot vpc ssh aws** more critical than ever. As devices become more intelligent and autonomous, relying on edge computing and artificial intelligence, the need for robust, scalable, and adaptable security frameworks will intensify. The future will likely see even tighter integration between cloud security services and edge devices, with AI-driven threat detection becoming standard practice. Emerging technologies like 5G will enable even greater numbers of devices to connect, demanding more sophisticated network segmentation and real-time threat analysis. Blockchain technology may also play a role in securing device identities and data integrity. Furthermore, the emphasis on regulatory compliance and data privacy (like GDPR and CCPA) will continue to shape how IoT data is collected, processed, and secured. Ultimately, the future of secure remote IoT lies in a proactive, layered, and automated security posture that can anticipate and neutralize threats before they impact operations. By continuously refining their AWS VPC, SSH, and overall IoT security strategies, organizations can not only mitigate risks but also unlock the full transformative potential of their connected world.Conclusion
The journey to securely manage and interact with remote IoT devices is complex, but with the powerful combination of **remoteiot vpc ssh aws**, organizations can build resilient and highly secure architectures. We've explored how AWS VPC provides essential network isolation and granular control through subnets and Network ACLs, creating a private haven for your IoT infrastructure. We've also delved into the critical role of SSH for secure remote access, emphasizing the paramount importance of robust SSH key management and best practices. Integrating these foundational elements with the broader AWS ecosystem, from IoT Core to advanced security services, enables a comprehensive approach to device management, data processing, and threat detection. By understanding the evolving threat landscape, meticulously designing your VPC, implementing stringent SSH security measures, and continuously monitoring your environment, you can ensure that your remote IoT deployments are not just operational, but truly secure. The principles of least privilege, defense in depth, and continuous vigilance are not merely suggestions but necessities for safeguarding your valuable IoT assets and the data they generate. Have you embarked on your own **remoteiot vpc ssh aws** journey? What unique challenges have you faced, and what solutions have you discovered? Share your experiences and insights in the comments below! Your contributions help enrich the community's understanding and foster best practices in this critical domain. If you found this article insightful, consider sharing it with your network or exploring other related articles on our site to deepen your knowledge of cloud security and IoT.Table of Contents
- The Evolving Landscape of IoT Security
- Understanding AWS VPC for IoT Isolation
- Secure Connectivity with SSH for Remote IoT Devices
- Integrating Remote IoT Devices with AWS Services
- Building a Secure Remote IoT Architecture with AWS
- Troubleshooting Common Remote IoT VPC SSH AWS Issues
- Advanced Security Considerations for Remote IoT Deployments
- The Future of Secure Remote IoT
- Conclusion
Related Resources:


Detail Author:
- Name : Prof. Eloise Nikolaus
- Username : sandy.rice
- Email : ezequiel.harris@gmail.com
- Birthdate : 1993-04-11
- Address : 7809 Davis Groves Apt. 056 South Loyal, SD 77188-9516
- Phone : 703-821-8302
- Company : Berge-Murray
- Job : Housekeeping Supervisor
- Bio : Et ratione ut placeat voluptas eaque. Excepturi cum temporibus et facilis. Veniam molestiae aut corporis ea dicta quam. Perferendis sunt aperiam et sit voluptas voluptate.
Socials
linkedin:
- url : https://linkedin.com/in/goldner1972
- username : goldner1972
- bio : Nostrum dicta nisi soluta.
- followers : 4620
- following : 2449
facebook:
- url : https://facebook.com/gusgoldner
- username : gusgoldner
- bio : Ut minus qui ut. Ullam hic enim suscipit recusandae.
- followers : 3439
- following : 344
instagram:
- url : https://instagram.com/gus_official
- username : gus_official
- bio : Soluta sit velit in. Ut id omnis odit harum.
- followers : 6485
- following : 108
twitter:
- url : https://twitter.com/gus_goldner
- username : gus_goldner
- bio : Sapiente eum provident voluptatem mollitia asperiores fugiat. Libero qui amet ut similique qui quia porro. Dolorum in rerum fuga ratione et est.
- followers : 4803
- following : 189