**In today's interconnected world, the ability to control and monitor devices from anywhere is not just a luxury but often a necessity. This is precisely where the concept of remoteiot behind router example in raspberry pi comes into play, offering a powerful and flexible solution for managing your smart devices. Whether you're a seasoned developer, a curious hobbyist, or simply someone looking to expand the capabilities of your smart home, understanding how to securely access your Internet of Things (IoT) devices when they are tucked away behind your home or office router is a fundamental skill.**
The challenge often lies in network configurations, specifically how routers manage incoming connections. However, with a versatile platform like the Raspberry Pi, these hurdles can be effectively overcome. This comprehensive guide will delve into the intricate details of setting up and managing remote access to your IoT devices, even when they are situated behind a router, ensuring both accessibility and robust security. By exploring various methods and best practices, you'll gain the knowledge to confidently implement your own remote IoT solutions.
Table of Contents
- The Necessity of Remote IoT: Why Behind a Router?
- Understanding the Network Barrier: NAT and Firewalls
- Core Strategies for Remote Access
- Remote IoT Behind Router Example in Raspberry Pi: A Practical Approach
- Implementing Reverse SSH Tunneling for Secure Access
- Security Best Practices for Your Remote IoT Setup
- Troubleshooting Common Remote Access Issues
- The Future of Remote IoT and Raspberry Pi Innovation
- Conclusion: Empowering Your IoT Journey
The Necessity of Remote IoT: Why Behind a Router?
The allure of remote IoT is undeniable. Imagine adjusting your home's thermostat from your office, monitoring your pet feeder while on vacation, or collecting sensor data from a remote location without physically being there. This level of control and insight is what drives the adoption of IoT. However, a common misconception is that IoT devices are inherently accessible from anywhere. In reality, most home and small office networks place devices behind a router, which acts as a protective barrier. This barrier, while crucial for security, also complicates direct external access.
- Laurine Nickel
- Aditi Mistry Nude Videocom
- Diva Flawless Nide Videos
- Aiditi Mistry Nude
- Kaitlyn Bubolz Leaks
Positioning an IoT device, like a Raspberry Pi, behind a router offers enhanced security. The router's Network Address Translation (NAT) and built-in firewall shield your internal network from unsolicited external connections, significantly reducing the attack surface. This is a fundamental principle of network security. Without this protection, every device on your network would be directly exposed to the vast and often hostile internet. Therefore, learning how to implement a remoteiot behind router example in raspberry pi isn't about bypassing security, but rather about intelligently navigating network configurations to achieve remote accessibility while maintaining a strong security posture. It's about striking the right balance between convenience and protection, ensuring your smart devices remain both useful and safe.
Understanding the Network Barrier: NAT and Firewalls
To truly grasp how to enable remote access to your Raspberry Pi and its connected IoT devices, it's essential to understand the core mechanisms that prevent it by default: NAT and firewalls.
Network Address Translation (NAT): Most home and small office networks use NAT. Your router receives a single public IP address from your Internet Service Provider (ISP). All devices on your internal network, however, have private IP addresses (e.g., 192.168.1.X). When an internal device wants to access the internet, the router translates its private IP to the public IP. Crucially, when external traffic tries to reach your public IP, the router doesn't know which internal device it's intended for, as it didn't initiate that connection. This is why direct incoming connections are blocked by default.
- Gali Gool Onlyfans
- Dr Gustavo Quiros Licona Facebook
- Wasmo Somali Muqdisho Telegram 2025
- Camilla Araujo Leaks
- Milena Rocha Onlyfans
Firewalls: Complementing NAT, your router's firewall acts as a digital bouncer, inspecting incoming and outgoing network traffic. It operates based on a set of rules, typically blocking any incoming connection that wasn't explicitly requested by an internal device. This proactive defense mechanism is vital for preventing unauthorized access, malware, and other cyber threats from penetrating your local network. Overcoming these barriers requires specific configurations that tell the router which incoming traffic to allow and where to direct it, forming the basis of any remoteiot behind router example in raspberry pi.
Core Strategies for Remote Access
Enabling remote access to your Raspberry Pi behind a router involves several established strategies, each with its own advantages, disadvantages, and security implications. Understanding these core methods is crucial for choosing the right approach for your specific IoT project.
- Port Forwarding: This is the most straightforward method. You configure your router to direct incoming traffic on a specific public port to a specific private IP address and port on your internal network (e.g., your Raspberry Pi's IP and SSH port). While simple, it exposes the target service directly to the internet, making it potentially vulnerable if not properly secured.
- Virtual Private Networks (VPNs): A VPN creates a secure, encrypted tunnel between your remote device and your home network. Instead of exposing individual services, you access your entire home network as if you were physically there. This is generally considered one of the most secure methods for remote access, as all traffic within the tunnel is encrypted.
- Cloud IoT Platforms (e.g., AWS IoT, Google Cloud IoT, Azure IoT Hub): These platforms provide a managed service for connecting and managing IoT devices. Devices connect outbound to the cloud platform using protocols like MQTT, and you interact with the devices through the cloud service's APIs or dashboards. This eliminates the need for direct incoming connections to your home network, as the communication is brokered by the cloud.
- Reverse SSH Tunneling: This method involves the Raspberry Pi initiating an outbound SSH connection to a publicly accessible server (a "jump server"). This connection creates a tunnel through which you can then connect back to the Raspberry Pi from the jump server, effectively bypassing NAT and firewalls without opening incoming ports on your router. It's a highly secure and flexible method.
- Third-Party Remote Access Services (e.g., TeamViewer, AnyDesk, Remote.It): These services provide pre-built solutions that handle the complexities of NAT traversal and secure connections. While convenient, they rely on a third-party server and may involve subscription fees.
Each of these strategies offers a viable path to achieve a functional remoteiot behind router example in raspberry pi. The best choice depends on your technical comfort, security requirements, and the specific nature of your IoT application.
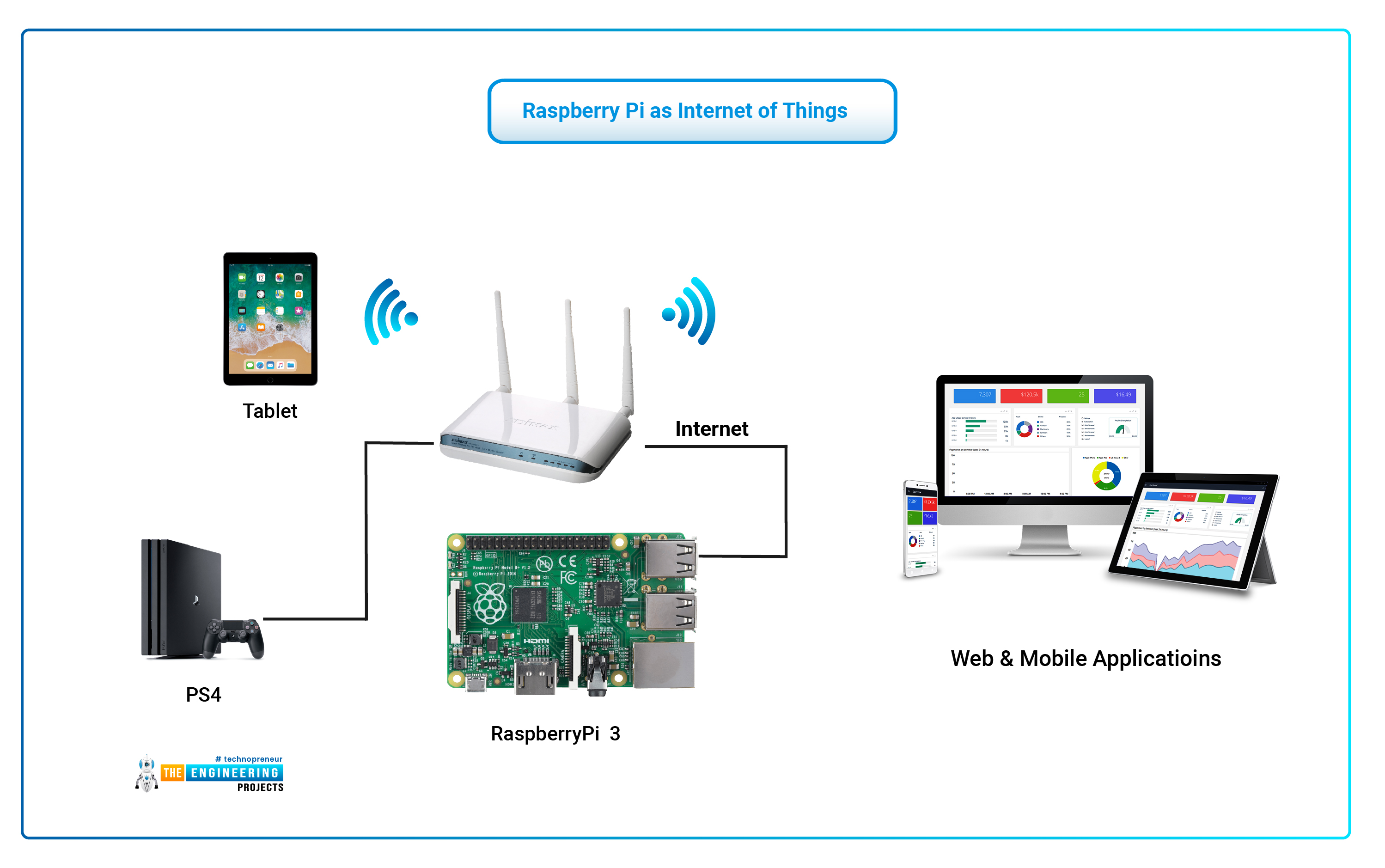
Remote IoT Behind Router Example in Raspberry Pi: A Practical Approach
This section provides a hands-on guide to implementing various methods for accessing your IoT devices remotely using a Raspberry Pi, even when it's situated behind a router. This example demonstrates how to set up a basic, yet powerful, remote IoT environment.
Setting Up Your Raspberry Pi for Remote Access
Before diving into specific remote access methods, ensure your Raspberry Pi is properly configured. This foundational setup is critical for any remoteiot behind router example in raspberry pi.
- Install Raspberry Pi OS: Flash a clean image of Raspberry Pi OS (formerly Raspbian) onto an SD card. Use tools like Raspberry Pi Imager for an easy process.
- Initial Setup: Connect your Pi to a monitor, keyboard, and mouse. Complete the initial setup wizard, including setting your locale, password, and Wi-Fi network.
- Enable SSH: SSH (Secure Shell) is essential for remote command-line access. You can enable it via the Raspberry Pi Configuration tool (
sudo raspi-config-> Interface Options -> SSH) or by creating an empty file namedsshin the boot partition of your SD card before booting. - Update and Upgrade: Always ensure your Pi's software is up-to-date. Open a terminal and run:
sudo apt update sudo apt upgrade -y - Assign a Static IP Address: For reliable remote access, your Raspberry Pi should have a static IP address on your local network. This prevents its IP from changing, which would break your remote connections. You can configure this in your router's DHCP reservation settings or directly on the Raspberry Pi by editing
/etc/dhcpcd.conf. For example:
(Replaceinterface wlan0 static ip_address=192.168.1.100/24 static routers=192.168.1.1 static domain_name_servers=192.168.1.1 8.8.8.8wlan0witheth0for wired connection, and adjust IP addresses to match your network.)
Method 1: Port Forwarding – The Direct Approach
Port forwarding is the simplest way to allow external traffic to reach a specific device on your internal network. While straightforward, it requires careful security considerations.
How it works: You tell your router to forward incoming connections on a specific external port (e.g., 2222) to a specific internal IP address (your Raspberry Pi's static IP, e.g., 192.168.1.100) and port (e.g., 22 for SSH).
Steps:
- Find Your Router's IP Address: This is usually your default gateway (e.g., 192.168.1.1).
- Access Router Settings: Open a web browser and enter your router's IP address. Log in with your administrator credentials (often found on a sticker on the router or in its manual).
- Locate Port Forwarding Settings: This section is usually under "Advanced," "NAT," "Firewall," or "Virtual Servers."
- Create a New Rule:
- Service Name: e.g., "Pi SSH Remote"
- External Port (or WAN Port): Choose a high, non-standard port (e.g., 2222, 22222). Avoid common ports like 22, 80, 443, as they are frequently scanned by malicious actors.
- Internal Port (or LAN Port): 22 (for SSH)
- Protocol: TCP
- Internal IP Address: Your Raspberry Pi's static IP (e.g., 192.168.1.100)
- Enable/Apply the rule.
- Find Your Public IP Address: Go to a website like
whatismyip.comfrom a device on your home network. - Test the Connection: From an external network (e.g., using mobile data on your phone or another Wi-Fi network), try to SSH to your Pi:
(e.g.,ssh pi@YOUR_PUBLIC_IP_ADDRESS -p YOUR_EXTERNAL_PORTssh pi@203.0.113.45 -p 22222)
Security Warning: Port forwarding directly exposes a service. Ensure your SSH on the Pi is secured with strong passwords or, even better, SSH key-based authentication. Regularly update your Pi's software. This is a simple remoteiot behind router example in raspberry pi but comes with inherent risks if not handled with care.
Method 2: VPN (Virtual Private Network) – The Secure Tunnel
Setting up a VPN server on your Raspberry Pi transforms it into a secure gateway to your home network, offering a much higher level of security compared to direct port forwarding.
How it works: When you connect to your Raspberry Pi VPN server from a remote location, your device creates an encrypted tunnel to your home network. All your internet traffic then flows through this tunnel, making it appear as if you are physically connected to your home network.
Steps (using OpenVPN, a popular choice):
- Install PiVPN: PiVPN is a script that simplifies OpenVPN (or WireGuard) installation on a Raspberry Pi.
Follow the on-screen prompts. You'll choose your VPN protocol (OpenVPN is robust), select your network interface, and decide whether to use your public IP or a DNS service (like No-IP or DuckDNS if your public IP changes).curl -L https://install.pivpn.io | bash - Generate Client Profiles: Once PiVPN is installed, use the command
pivpn addto create new client configurations for your remote devices (laptop, phone). This will generate.ovpnfiles. - Port Forward VPN Port: You will need to port forward the VPN server's port on your router. For OpenVPN, this is typically UDP port 1194. Forward this port from your router's public IP to your Raspberry Pi's static IP (e.g., 192.168.1.100) on port 1194 UDP.
- Install VPN Client: Install an OpenVPN client on your remote device (e.g., OpenVPN Connect app on mobile, OpenVPN GUI on Windows, Tunnelblick on macOS).
- Import Profile and Connect: Import the generated
.ovpnfile into your client and connect. Once connected, you should be able to access other devices on your home network, including your IoT devices, using their private IP addresses (e.g., 192.168.1.X).
This method provides a robust remoteiot behind router example in raspberry pi, offering end-to-end encryption and the ability to access any device on your home network securely.
Method 3: Cloud IoT Platforms and MQTT – The Managed Solution
For scalable and robust IoT deployments, integrating your Raspberry Pi with a cloud IoT platform using MQTT (Message Queuing Telemetry Transport) is an excellent choice. This approach avoids direct incoming connections to your router entirely.
How it works: Your Raspberry Pi, acting as an IoT gateway or device, connects outbound to a cloud-based MQTT broker. It publishes sensor data to specific "topics" and subscribes to other topics to receive commands. Your remote application also connects to the same cloud MQTT broker, publishing commands and subscribing to data topics. The cloud broker facilitates secure, bidirectional communication without needing any port forwarding.
Steps (Conceptual, using Paho MQTT client on Pi):
- Choose a Cloud IoT Platform: Options include AWS IoT Core, Google Cloud IoT Core, Azure IoT Hub, Adafruit IO, or even a self-hosted MQTT broker on a VPS. For simplicity, let's assume Adafruit IO for this conceptual example due to its ease of use for hobbyists.
- Set up Cloud Platform:
- Create an account on Adafruit IO.
- Create a new "Feed" (e.g., "temperature-sensor") for your sensor data.
- Note your Adafruit IO username and AIO Key (API key).
- Install MQTT Client on Raspberry Pi:
pip3 install adafruit-io paho-mqtt - Python Script on Pi (example for publishing data):
import time import random from Adafruit_IO import Client, Feed # Set up Adafruit IO ADAFRUIT_IO_USERNAME = 'YOUR_ADAFRUIT_IO_USERNAME' ADAFRUIT_IO_KEY = 'YOUR_ADAFRUIT_IO_KEY' aio = Client(ADAFRUIT_IO_USERNAME, ADAFRUIT_IO_KEY) # Define the feed TEMPERATURE_FEED = 'temperature-sensor' print(f"Publishing to feed: {TEMPERATURE_FEED}") while True: try: # Simulate reading a sensor temperature = random.uniform(20.0, 30.0) print(f"Publishing temperature: {temperature:.2f}") aio.send_data(TEMPERATURE_FEED, temperature) time.sleep(10) # Publish every 10 seconds except Exception as e: print(f"Error publishing data: {e}") time.sleep(5) # Wait before retrying - Remote Access/Control:
- You can view the data on your Adafruit IO dashboard from any web browser.
- To send commands to your Pi (e.g., turn on an LED), create another feed (e.g., "led-control") and have your Pi subscribe to it. Your remote application (another script, a web app, or even the Adafruit IO dashboard) can then publish to this feed, and your Pi will receive the command.
This method provides a highly scalable and secure remoteiot behind router example in raspberry pi, leveraging the robust infrastructure of cloud providers. It's ideal for projects requiring reliable data ingestion and command delivery.
Implementing Reverse SSH Tunneling for Secure Access
Reverse SSH tunneling is an ingenious and highly secure method to access your Raspberry Pi behind a router without needing to configure port forwarding on your home router. It's particularly useful when you don't have control over the router or when dynamic public IP addresses are an issue.
How it works: The Raspberry Pi initiates an SSH connection outwards to a publicly accessible server (often called a "jump server" or "bastion host") that you control. This connection creates a persistent tunnel. You can then connect to a specific port on your jump server, and that connection will be forwarded back through the tunnel to your Raspberry Pi. Essentially, the Pi "calls out" and leaves a door open for you to come back in.
Requirements:
- A Raspberry Pi (your local device).
- A publicly accessible server (e.g., a cheap VPS from DigitalOcean, Linode, Vultr, or AWS EC2 micro instance) with SSH access. Let's call this your "Jump Server."
Steps:
- Prepare Your Jump Server:
- Ensure SSH is running and accessible (port 22 by default).
- For security, consider creating a dedicated user for the tunnel and disabling password authentication for SSH, relying solely on SSH keys.
- Edit
/etc/ssh/sshd_configon the Jump Server to allow gateway ports (if you want to access the Pi from other machines via the jump server):
Restart SSH service:GatewayPorts yessudo systemctl restart sshd
- Set up the Reverse Tunnel on Raspberry Pi: The Raspberry Pi will initiate the connection to the Jump Server. You'll want this connection to be persistent.
Let's break this down:ssh -N -R 2222:localhost:22 user@your_jump_server_ipssh: The SSH command.-N: Do not execute a remote command (just forward ports).-R 2222:localhost:22: This is the reverse tunnel. It means "forward port 2222 on the remote (jump) server back to port 22 on the local (Raspberry Pi) machine."user@your_jump_server_ip: Your username and IP address of the Jump Server.
autosshor a systemd service to ensure the tunnel reconnects if it drops.sudo apt install autossh autossh -M 0 -o "ExitOnForwardFailure yes" -o "ServerAliveInterval 30" -o "ServerAliveCountMax 3" -N -R 2222:localhost:22 user@your_jump_server_ip - Access Your Raspberry Pi Remotely: From any machine on the internet, you can now SSH into your Raspberry Pi via the Jump Server:
This command connects to port 2222 on your Jump Server, which then forwards the connection through the established tunnel to port 22 (SSH) on your Raspberry Pi.ssh pi@your_jump_server_ip -p 2222
This method provides a very secure and robust remoteiot behind router example in raspberry pi, as no incoming ports are opened on your home router, and all traffic is encrypted within the SSH tunnel. It's an excellent choice for sensitive applications or when router configuration is difficult.
Security Best Practices for Your Remote IoT Setup
Regardless of the method chosen for your remoteiot behind router example in raspberry pi, security must be paramount. IoT devices are increasingly targeted by cybercriminals due to their often-lax security. Implementing these best practices will significantly enhance the trustworthiness and integrity of your setup:
- Strong, Unique Passwords: Never use default passwords. Use long, complex passwords for your Raspberry Pi, router, and any cloud IoT accounts. Consider a password manager.
- SSH Key-Based Authentication: For SSH access, disable password authentication and use SSH keys. This is far more secure than passwords. Generate a key pair, copy the public key to your Pi, and use the private key on your client.
- Change Default SSH Port: If using port forwarding for SSH, change the default SSH port (22) to a non-standard, high-numbered port (e.g., 22222). This reduces automated scanning attempts.
- Keep Software Updated: Regularly run
sudo apt update && sudo apt upgrade -yon your Raspberry Pi to ensure all software, including the kernel and security patches, are up-to-date. Update your router's firmware as well. - Minimal Open Ports: Only open ports that are absolutely necessary. If using port forwarding, ensure only the required ports are open and directed to the correct device. Close them when not in use if possible.
- Firewall on Raspberry Pi (UFW): Install and configure a local firewall on your Raspberry Pi (e.g., UFW - Uncomplicated Firewall) to restrict incoming and outgoing connections at the device level.
sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow ssh # Or your custom SSH port sudo ufw enable - Use a VPN: As discussed, a VPN provides an encrypted tunnel, making it one of the most secure ways to access your home network remotely.
- Monitor Logs: Periodically check system logs on your Raspberry Pi (e.g.,
/var/log/auth.logfor SSH attempts) for suspicious activity. - Disable Unused Services: Turn off any services on your Raspberry Pi that you don't use (e.g., VNC, Samba if not needed).
Related Resources:


Detail Author:
- Name : Jessika Daugherty MD
- Username : rachel63
- Email : rosie73@robel.com
- Birthdate : 2006-02-19
- Address : 48075 Teresa Radial Robelview, VA 35454
- Phone : 1-669-720-4748
- Company : Bode, Kilback and Johnston
- Job : Sales Manager
- Bio : Aperiam beatae minus dolores magnam. Voluptas tempore sit consequatur id molestias. Aut molestiae quo aut reprehenderit exercitationem soluta voluptatibus.
Socials
tiktok:
- url : https://tiktok.com/@dwelch
- username : dwelch
- bio : Sed sunt aliquid saepe consequuntur ratione explicabo sed.
- followers : 750
- following : 1646
linkedin:
- url : https://linkedin.com/in/dwelch
- username : dwelch
- bio : Deserunt vitae facilis illo velit architecto.
- followers : 1179
- following : 1480
instagram:
- url : https://instagram.com/dwelch
- username : dwelch
- bio : Eos consequatur nihil nostrum eos consequatur cum. Dolore et dolorum natus laudantium.
- followers : 5097
- following : 957