Connecting devices that are far away, sometimes in places you can't easily get to, is a big deal these days. Picture a sensor out in a field, or a camera watching over something in a distant spot. Making sure these gadgets can talk back to you, and that their conversations stay private, is a really important piece of the puzzle. This is where thinking about things like a virtual private cloud, secure ways of reaching them, and cloud services comes into play for your distant gadget setup.
You know, it's almost like having a secret pathway for all your gadget communications. Without a good way to keep those pathways private and safe from prying eyes, your important information could be out in the open. Nobody wants their distant gadgets to be easy targets for folks who might want to mess with them or steal what they are saying. So, setting up a solid, protected line for these things is something you really have to consider.
This is where the big cloud providers, with their tools, can lend a hand. They give you the building blocks to create those private spaces and secure ways to get in. We're talking about setting up a special, isolated area just for your gadgets within a larger cloud system, and then using a very particular kind of secure connection to talk to them. It’s all about making sure your remote gadget network, especially when it lives in the cloud, stays just for you, basically.
Table of Contents
- What Is Remote IoT, Really?
- Why a VPC for RemoteIoT Matters
- How SSH Helps with RemoteIoT AWS Access?
- Getting Your RemoteIoT VPC Ready
- Making the Link to RemoteIoT Devices with SSH
- Keeping Your RemoteIoT AWS Safe and Sound
- Looking Past the Basics for RemoteIoT AWS
- A Peek at RemoteIoT Possibilities
What Is Remote IoT, Really?
So, what do we mean when we talk about "remote gadgetry" or "remote IoT"? Well, it's about all those physical things that have sensors, software, and other ways of linking up with other systems over the internet. These aren't just the gadgets sitting on your desk; they are often out in the world, far from where you might be. Think about, say, a smart thermometer in a cold storage unit many miles away, or a motion detector in a building that's usually empty. These things need to send their readings back, and sometimes they need to get new instructions too. This kind of gadgetry helps businesses keep tabs on things, automate processes, and collect important pieces of information without needing a person right there. It’s a pretty big deal for many different kinds of work, actually, letting folks gather information from places they just couldn't before.
The beauty of this setup is that it lets you extend your reach. You can have eyes and ears in places that would otherwise be out of touch. Imagine a water quality sensor in a distant river, or a machine part that tells you it needs fixing before it breaks down. All of these are examples of distant gadgetry at work. The information they gather can help people make smarter choices, save money, and even prevent problems before they start. It's a way of making our physical world a bit more intelligent, more responsive, and, you know, more connected in a very useful way. This is why getting these distant gadgets to talk securely is so very important.
Why a VPC for RemoteIoT Matters
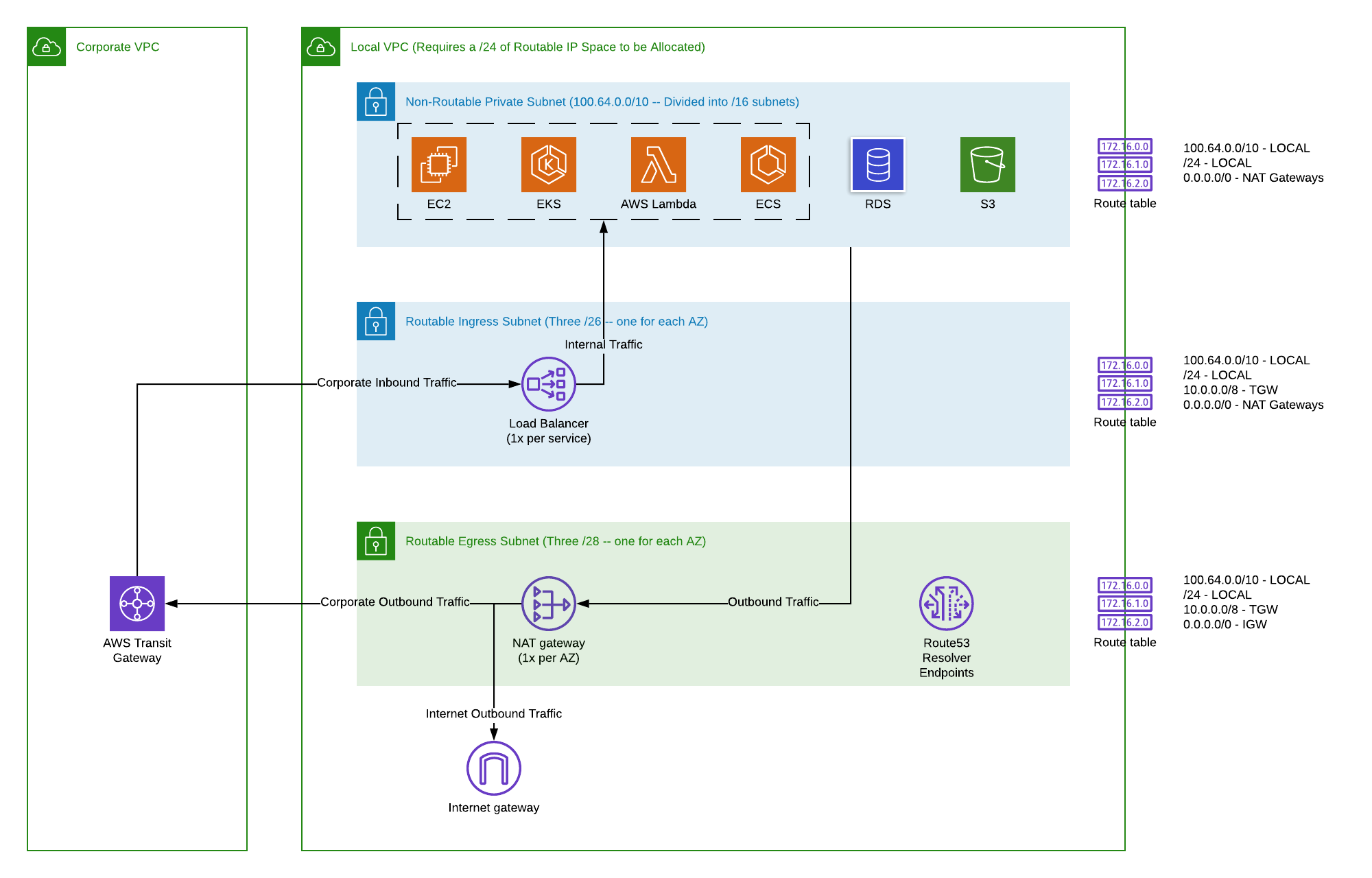
Now, let's talk about why having a special, isolated space, what people call a Virtual Private Cloud (VPC), is such a good idea for your distant gadget setup. Think of it like this: when you use a big cloud service, it's a bit like living in a huge apartment building. There are lots of other people (other businesses) living there too, and while everyone has their own apartment, the hallways and common areas are shared. A VPC is like having your very own floor in that building, with your own private elevator and a locked door that only you have the key to. This means your distant gadget communications and the systems that manage them are kept separate from everyone else's. This separation is key for keeping things safe. It helps make sure that only your gadgets and your people can talk to your specific resources, and that no one else can accidentally or purposely get in the way. It’s a way of giving your distant gadget setup a private home within the larger cloud environment, which is a rather comforting thought.
This private area gives you a lot of control over who can get in and what can happen inside. You can set up your own rules for how information flows, what kind of access is allowed, and where different parts of your system live. For your distant gadget setup, this means you can build a secure boundary around your devices, your data collection points, and any applications that work with them. It’s about building a digital fence, if you will, around your important pieces. This level of control is pretty important when you're dealing with sensitive information or critical operations that rely on your distant gadgets. So, having this dedicated space just for your distant gadget cloud activities gives you a lot of peace of mind, essentially.
How SSH Helps with RemoteIoT AWS Access?
So, you've got your private cloud space for your distant gadgets. But how do you actually get into the systems that manage those gadgets, especially if they're sitting far away in the cloud? This is where something called SSH, or Secure Shell, comes in very handy. Imagine you need to send a secret message across a busy public park. You wouldn't just shout it out, would you? SSH is like putting that message inside a super-strong, locked box, and then sending it through a private, invisible tunnel right to the person it's meant for. It creates a secure way to talk to your cloud servers, like the ones in your distant gadget cloud setup, over a public internet connection. This means that even if someone were listening in on the public internet, they wouldn't be able to understand what you're saying because it's all scrambled up and protected. It's a way of making sure your commands and any information you send back and forth stay private and can't be tampered with. This secure link is a big part of keeping your distant gadget operations safe, you know.
Using SSH means that when you connect to a server in your distant gadget cloud setup, the link between your computer and that server is encrypted. This is like having a secret code that only your computer and the server know, making it impossible for anyone else to read your conversation. It's a standard way for system administrators and developers to manage servers remotely, and it's especially useful for cloud environments where you're not physically next to the machines. For anything related to your distant gadget cloud setup, whether it's checking on a system, running a script, or moving files around, SSH provides that necessary layer of protection. It really is a fundamental tool for safe remote interaction, giving you a lot of comfort when you're working with your cloud resources, basically.
Getting Your RemoteIoT VPC Ready
Setting up your own private cloud area for your distant gadget operations might sound a bit involved, but it's really about following a few steps to make sure everything is in its right place. First, you'll want to decide on the size of your private area. This means choosing a range of internet addresses that will be unique to your distant gadget cloud space. It's like picking out a plot of land for your house; you need to know how big it will be. Then, you'll break that big plot down into smaller sections, which are like different rooms or yards within your property. These smaller sections help you organize your resources and apply different safety rules to different parts of your distant gadget setup. You'll also set up special gateways that let your private area talk to the wider internet, but only in ways you approve. It’s all about creating a controlled environment where your distant gadget operations can thrive without being exposed to unnecessary risks, you see.
Once you have the basic layout of your private cloud area, you'll add things like routing tables, which are like maps that tell information where to go within your private space and out to the internet. You'll also put in place security groups, which are like digital bouncers that decide who gets to come in and out of specific parts of your distant gadget cloud setup. These groups let you specify exactly which kinds of traffic are allowed, making sure that only the necessary communications can happen. For example, you might only allow SSH connections from specific locations, keeping your management access very tight. This careful preparation of your private cloud area is a really important step in building a safe and well-organized home for all your distant gadget activities, ensuring that your distant gadget cloud setup is ready for action, more or less.
Making the Link to RemoteIoT Devices with SSH
Once your private cloud area is all set up, the next step is to actually make that secure link to your distant gadget devices using SSH. This usually involves having a special pair of digital keys: one that stays on your computer, kept very private, and another that lives on the server or device you want to reach within your distant gadget cloud setup. When you try to connect, these two keys talk to each other, making sure you are who you say you are before letting you in. It's a much safer way to get into a system than using just a password, which can sometimes be guessed or stolen. With these keys, you can open up a secure tunnel directly to your distant gadget management server. This tunnel is where all your commands and any information you need to send or receive will travel, all hidden away from prying eyes. This process helps keep your distant gadget operations running smoothly and safely, which is pretty important.
To get this going, you'll typically use a command-line tool on your computer. You just type a simple instruction, pointing to your private key and the address of the server in your distant gadget cloud setup. The system then handles all the complex parts of setting up that encrypted tunnel. Once you're connected, it's like you're sitting right in front of that distant server, even if it's thousands of miles away. You can run programs, check logs, or make changes, all through that secure SSH link. This way of working is really efficient and, more importantly, it helps keep your distant gadget system safe from unwanted intrusions. It's a fundamental part of managing any cloud-based distant gadget solution, giving you direct, protected control over your resources, basically.
Keeping Your RemoteIoT AWS Safe and Sound?
So, how do you make sure your distant gadget setup, especially when it's living in the cloud, stays safe and sound? It's not just about setting things up; it's also about keeping an eye on them and making smart choices as you go. One big part of this is managing who can do what. You want to give people just enough permission to do their jobs, and no more. This is like giving someone a key only to the rooms they need to enter, not the whole house. For your distant gadget cloud activities, this means carefully setting up user accounts and roles, making sure that if someone only needs to look at data, they can't accidentally or purposely change anything important. This principle of "least privilege" is a cornerstone of good security, and it's something you should always keep in mind for your distant gadget setup. It's a bit like making sure every door has the right lock, you know.
Another important aspect is regularly checking on your systems. Just like you'd check your car's tires, you need to look at your distant gadget cloud setup to make sure everything is running as it should be and that there are no unexpected visitors. This includes reviewing logs, which are like diaries of everything that happens on your servers, and keeping your software up to date. Outdated software can have weaknesses that bad actors might try to use to get into your distant gadget system. So, staying on top of updates is a pretty simple but very effective way to keep things protected. It's also a good idea to have plans for what to do if something does go wrong, like having backups of your important information. Taking these steps helps ensure your distant gadget cloud setup remains a safe and reliable place for your devices to operate, more or less.
Looking Past the Basics for RemoteIoT AWS
While setting up your private cloud area and using secure ways to get in are excellent starting points for your distant gadget operations, there's a whole lot more you can think about to make your system even better. For instance, consider how your distant gadgets actually send their information to the cloud. You might use special services that are built just for gadget communication, which can handle a huge number of devices and make sure their messages arrive reliably. These services often have their own ways of keeping things safe, adding another layer of protection on top of your private cloud area and secure access methods. Thinking about the entire path your information takes, from the gadget itself all the way to where it's stored and used, helps you spot any weak points and make them stronger. It’s about building a complete and very thoughtful system for your distant gadget needs, you know.
You can also think about automating some of the tasks involved in managing your distant gadget cloud setup. For example, instead of manually connecting to each server to check on things, you could set up automated tools that do it for you, alerting you only when something needs your direct attention. This can save a lot of time and help you respond more quickly to any issues. Furthermore, you might explore ways to make your system more resilient, so that if one part of it stops working, the whole thing doesn't fall apart. This could involve having duplicate systems ready to take over, or spreading your resources across different physical locations within the cloud. These kinds of considerations help ensure your distant gadget operations can keep going, even when unexpected things happen, which is pretty important for long-term success, essentially.
A Peek at RemoteIoT Possibilities
With a solid foundation for your distant gadget cloud setup, the possibilities really start to open up. Imagine being able to monitor environmental conditions in places that are hard to reach, like deep within a forest or at the top of a mountain, all from your desk. Or perhaps keeping tabs on the health of industrial machinery in a factory without needing someone to walk around and check each piece by hand. Distant gadgetry, supported by a private cloud area and secure access, makes these kinds of things not just possible, but quite practical. It allows businesses and organizations to gather information and control things in ways that were once very difficult or simply too expensive. This shift means more informed choices, better efficiency, and new ways of doing things that can really make a difference, you know.
The information collected by these distant gadgets can be used for all sorts of smart applications. You could use it to predict when a piece of equipment might fail, allowing you to fix it before it causes a costly shutdown. Or, you could optimize energy use in a building by reacting to real-time temperature and occupancy data. The more information you can gather from the physical world, and the more securely you can manage those distant gadgets, the more intelligent your operations can become. It's about connecting the physical world with the digital one in a safe and meaningful way, creating systems that are more responsive and, in some respects, more capable than ever before. This kind of setup truly expands what's possible for many kinds of work, giving folks new ways to solve old problems, basically.
Related Resources:


Detail Author:
- Name : Elmo Koch
- Username : daren.grant
- Email : goyette.jeremie@bartell.com
- Birthdate : 1990-02-15
- Address : 7394 Bode Hills West Jocelyn, HI 59142
- Phone : 1-361-499-0257
- Company : Mann-Altenwerth
- Job : Protective Service Worker
- Bio : Sed ipsa nesciunt est qui aut. Quam officia nobis aut labore deleniti. Sit iste quisquam omnis ipsa.
Socials
tiktok:
- url : https://tiktok.com/@malika.streich
- username : malika.streich
- bio : Reiciendis ducimus vel et reiciendis. Aut ullam minus omnis quia laborum.
- followers : 4995
- following : 1324
linkedin:
- url : https://linkedin.com/in/malikastreich
- username : malikastreich
- bio : Corrupti id sequi facere minus odit ex.
- followers : 5375
- following : 2307
twitter:
- url : https://twitter.com/streichm
- username : streichm
- bio : Ea veniam quisquam tempora fugit iusto numquam aut. Assumenda quidem dicta optio ullam est est hic. Nisi libero ut sint.
- followers : 2715
- following : 1585
facebook:
- url : https://facebook.com/malikastreich
- username : malikastreich
- bio : Eos enim suscipit vitae iusto architecto dolorum. Sint vel similique quia.
- followers : 3739
- following : 2816
instagram:
- url : https://instagram.com/streichm
- username : streichm
- bio : Iste odit dignissimos et. Et libero dolor placeat nihil alias delectus beatae. Ut esse quia enim.
- followers : 6421
- following : 773